Cybersecurity Policy
With the use of the internet and technology becoming an integral part of daily activities, it is prudent to practice good cyber hygiene habits to protect your online identity and data. Below are some cyber hygiene tips:
1. Check the Website Address
Similar versions of a login portal can be re-created by hackers or scammers. They may vary the login web address to look almost identical to the actual web page. It is strongly recommended to check for the following when visiting the web-based AGX (the “Exchange”) login portal:
(a) The address bar of the browser is showing https://agx.co or https://www.agx.co
(b) There is a padlock icon displayed before the web address
![]()
If either one of the above is incorrect or looks suspicious, please do not proceed to log into your account.
2. Password Management
A strong password should be used for your login credentials along with good password management practices. Below are some pointers to consider:
(a) When creating a password, it should be a minimum of 12 characters with at least:
i. 1 alphabet character
ii. 1 numeric character
iii. 1 upper case character
iv. 1 lower case character
v. 1 special character (e.g. “@”, “#”, “!”, “%”, “^”, “$”, etc.)
(b) Using a passphrase as the password with password characteristics mentioned in part a above
(c) Avoid using easily available information of yourself, e.g. your date of birth, your residential address, your full name or in part spelt backwards, etc
(d) Changing your password on a regular basis
(e) Do not leave your password or password hint written on a piece of paper in the open or publicly available for others to see
(f) Using a password management tool or a password vault
If you forgot your password, please use the available password reset link or instructions found at after verifying the authenticity of the URL as recommended above.
3. Monitor Account Activity
It is good practice to monitor your account activities closely and report any suspicious account activity. If you suspect your account has been compromised or if someone else has unauthorised access to your account, please change your password and notify us at info@agx.co as soon as possible.
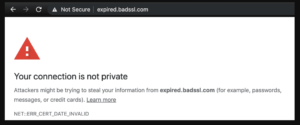
4. Security Certificate Warning
If you see a warning like the one below, do not interact further with the website. Instead, contact us immediately at info@agx.co.
5. Other Security Measures Include:
(a) Install anti-virus and firewall software, which are regularly updated, on the computers and mobile devices used to access the Exchange
(b) Regularly update the operating system on the computers and mobile devices used to access the Exchange
(c) Avoid jail breaking or rooting your mobile devices
(d) Avoid installing software and/or apps that are not from trusted sources
(e) Avoid using public computers or unsecured public Wi-Fi networks when accessing your account
(f) Using a Virtual Private Network (VPN) to encrypt the connection when accessing the Exchange on your computer and/or mobile devices
(g) Using an encryption algorithm with a key length of 256 bits or more to encrypt confidential information or personal information when sharing through email
6. Identifying and Preventing Phishing Attacks
Phishing is a method by which cybercriminals attempt to trick potential victims into divulging sensitive information, such as account names, passwords and bank account information. Phishing attempts can occur via email, phone calls, instant messages, social media platforms and more. Phishing attempts often also include a malicious link or attachment that infects the user system with malware, trojan or zero-day vulnerability exploit which may lead to ransomware attacks. Cybercriminals may also attempt to impersonate family members, friends, government officials or even an Exchange personnel. The Exchange’ personnel will never ask for your username, password, OTP (if applicable) or log-in credentials. Please email or contact the Exchange immediately if you have any suspicion to believe that you have been contacted by someone impersonating any Exchange personnel.
Below are some recommendations to protect yourself from phishing attacks:
(a) Check the sender’s email address
Check if you know the sender of any given email and verify the originating email address is correct. Phishing attacks are often sent from email addresses that are different from the domain name of the company or organization the sender is passing him or herself off as. In some instances, they may create and use domain names that are similar but not identical to the legitimate one (e.g. AGXX.co instead of AGX.co). Do not open emails from addresses that are not familiar to you.
(b) Pay attention to the language
Scrutinize the language used by the sender by looking out for grammatical or spelling errors in the communicated message. These mistakes in the message may be a result of a translation from a foreign language or a deliberate attempt to evade filters to block such attacks.
(c) Appeals to emotions
Pay close attention to the tone of the email. Promises of financial rewards, immediacy of urgency or a threat of serious consequences may be used to emotionally manipulate victims into doing their bidding.
(d) Be careful of attachments
Phishing emails very often require the recipients to take further actions, such as clicking or opening email attachments.
The attachments may contain viruses, spy software, and malware. These attachments typically have file extensions, such as “.exe”, “.zip” or “.pdf”. You should avoid opening attachments that you suspect may be illegitimate. It is recommended to run a malware scan on attachments using your anti-virus software before opening the attachments.
(e) Verify any embedded link before clicking
By moving your mouse cursor over the link and not clicking on it, you can check the authenticity of embedded link. Alternatively, you may access the Exchange’s website by manually typing the web address into your browser’s address bar.
If you receive a phishing email or other message that purports to come from the Exchange, please contact us at info@agx.co.
